Re: Filter Out Bot Clicks - Require Email Open?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We've recently started seeing a high number of clicks generated by bots. We have many smartcampaigns that fire off of clicks link in email. Would requiring clicks link in email AND opened an email in the past day resolve this? At least some of it? What other solutions have people found? Is there an item on the roadmap to automatically filter these out?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As many people have already said in response, a fully reliable solution is simply not present. I do however like the suggestion made in a previous discussion on this topic to include a 1 pixel image in your email template (blending into the background) with a url behind it. The logic is this link is not visible, so a normal human being would not click on it. Therefore any person clicking this link would be highly suspected to be a bot.
Does anyone have experience with this solution and its accuracy?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The pixel tells you that one hit was from a mail scanner, but it doesn't tell you which subsequent hits (and even prior hits, depending on scanner behavior) are from the mail scanner vs. interactive human.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That one pixel...or honeypot...has proven useful in creating the Bot identification program for us but deciphering whether a person identified as a bot actually follows up usually pinpointed by filtering those who (in our case) filled out a form (gated asset.) Now if we have a non-gated asset/email then it is harder to identify if anyone in the bot list followed it up with an actual click on a link. I'm open to hear suggestions...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is entirely true. It serves mainly to identify the suspected leads where mail scanners are active. You would need to further analyse these records to see the rest of their behaviour pattern and decide whether you want to exclude the entire lead from scoring on clicks or not. By no means a perfect solution, but from what I have seen so far the most likely to correctly identify leads with mail scanners running.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
As that number approaches 100% it doesn't help that much. 🙂
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Might be different in different countries, doesn't seem to be that widespread around here yet. Mostly some large international companies, but SME not so much.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That's assuming you know when the scanner is being used.
Think about what you're trying with the pixel: any HTML rendering engine knows exactly how large that will appear to the end user (i.e. it's not meant to be clicked) without following it. So the correct security tactic is to ignore it, to not send any more signals upstream.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Interesting point. Only proves that it is extremely difficult to really catch the right people. I'm starting to warm up to your suggestion to exclude email clicks from scoring and success attribution alltogether.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @cblack
In order to track Bot clicks, simply create Bot likelihood Campaigns with clicks counter and visits counter and then based on clicks and visits counting, decide whether the lead is bot or not.
For example :
Bot Likelihood is high when someone is clicking CTA multiple times and visiting page is empty (or not recorded in marketo)
Bot Likelihood is low when someone receives future email (email is delivered is recorded into marketo)
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What you are describing makes sense but it also sounds like a manual process to review and clean up. I am looking for something that at least improves the situation and is automated.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
There's no automated (let alone fully accurate) method. Remember, the whole idea of mail scanning is to seamlessly impersonate a human to see if the payload is malicious. Anything you can do in real-time to detect a scanner, a malicious operator can do as well, making the scanner meaningless.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I've stopped using email clicks as a means of measuring success and have been using page visits instead (as in visited page with utm parameter string indicating the visit came from the email). I know bots an also cause page visits but until recently I hadn't been seeing it. Now that's changed in the Marketo instance of at least one of my clients. Has anyone developed a way to automatically identify page visits from bots?
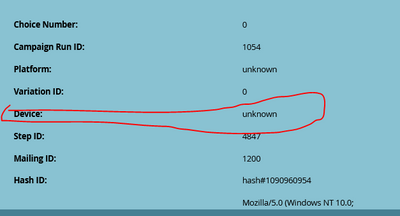
Secondly, back to the issue of clicks, I have a client asking me if it means anything with regard to "bot or not" when the click comes from an "unknown device" - as in this screenshot from the "click email" event in an activity log:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Now that's changed in the Marketo instance of at least one of my clients. Has anyone developed a way to automatically identify page visits from bots?
It's not possible to automatically identify a single pageview, as it's deliberately designed to use a headless browser and look just like an interactive (human) pageview.
People don't realize that a scanner that is unable to parse HTML + JavaScript that's found in the initial request (the request to the branding domain) is worthless. That first request fetches the branding domain page, which in turn does an immediate JavaScript-powered redirect to the original target URL. So if you want to check whether the first content shown to the user is malicious, you must at least follow the JS redirect and load the next page in full.
Secondly, back to the issue of clicks, I have a client asking me if it means anything with regard to "bot or not" when the click comes from an "unknown device" - as in this screenshot from the "click email" event in an activity log:
It just means the device (derived from the User-Agent) isn't in the list of known devices; it may be a mail scanner but since correctly functioning mail scanners take care to use known User-Agents, not worth filtering on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
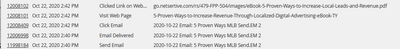
@SanfordWhiteman Thank you, Sandy! Another question - do link scanners sometimes also go on to click links on the web page linked to by the email? We're wondering if this PDF download is a bot based on the timing.
If so, wow. Link scanners don't fill out forms, too, do they?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Thank you, Sandy! Another question - do link scanners sometimes also go on to click links on the web page linked to by the email?
Not links that aren't followed (automatically) when a human hits the page. AFAIHave seen thus far.
If so, wow. Link scanners don't fill out forms, too, do they?
Not if the form typically requires a button push, that would be a horrible security risk.
The idea is to mimic actions that don't require end-user interaction.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi @SanfordWhiteman - This is a snippet from an activity log that caused me to ask if a bot could visit a page and then go on to click a link on the page. It's the time stamps that raise suspicion:
What do you think?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
What's up with the *-TY page? Isn't that itself a Thank You that wouldn't be linked directly in the email, or is it a misnomer?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
In addition to my above post, this may not be the 100% accurate/reliable way and would be great to have more thoughts.
- Copyright © 2025 Adobe. All rights reserved.
- Privacy
- Community Guidelines
- Terms of use
- Do not sell my personal information
Adchoices