- Marketing Nation
- :
- Products
- :
- Blogs
- :
- Product Blogs
- :
Don’t get bitten by your company’s DMARC subdomain ("sp") policy
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
The question lurks: Should you send mail From: user@example.com or switch to From: user@marketing.example.com?
And the answer remains: It depends.
First off, using a subdomain will not keep you off block lists. Domain-based lists always block the parent domain (a.k.a. shortest private suffix) as they’re quite aware of this attempt to dodge. “Reputation separation” via subdomains isn’t a thing.
There are still valid reasons to choose a subdomain, though:
- Easier Housekeeping: You want to quickly identify which of your services sent an email in case a recipient complains. Using SPF + DKIM + DMARC, you can ensure that Marketo only uses marketing.example.com, sales enablement only uses outreach.example.com, resellers use partners.example.com, and so on. (And any unknown subdomain must be rogue.)
- Reply Tracking: If you’re using reply-tracking software, replies must go to a specialized MX for marketing.example.com. There, OOO and similar messages are processed automatically. Human replies can go through a sentiment classifier and/or get forwarded to an attended mailbox @example.com.
But it’s almost too easy to switch to sending from a subdomain! Marketo will let you start sending From: any domain or subdomain, no (mandatory) questions asked. But your existing DMARC subdomain policy may kill deliverability from that subdomain, and you might not notice in spot checks.
A solid starting point
Assume the main corporate domain is marketo-dkim-demo.com (I registered that domain just for this post!) and you currently send like this:
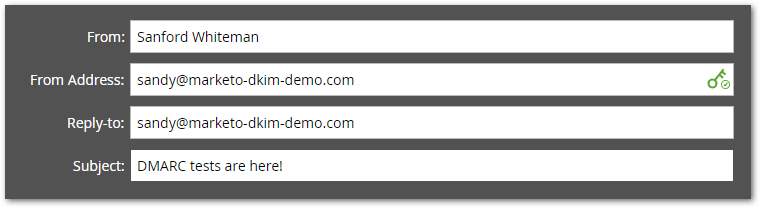
Your DKIM TXT record for m1._domainkey.marketo-dkim-demo.com is set up and verified:

And you also have a very simple DMARC TXT record at _dmarc.marketo-dkim-demo-com:[1]
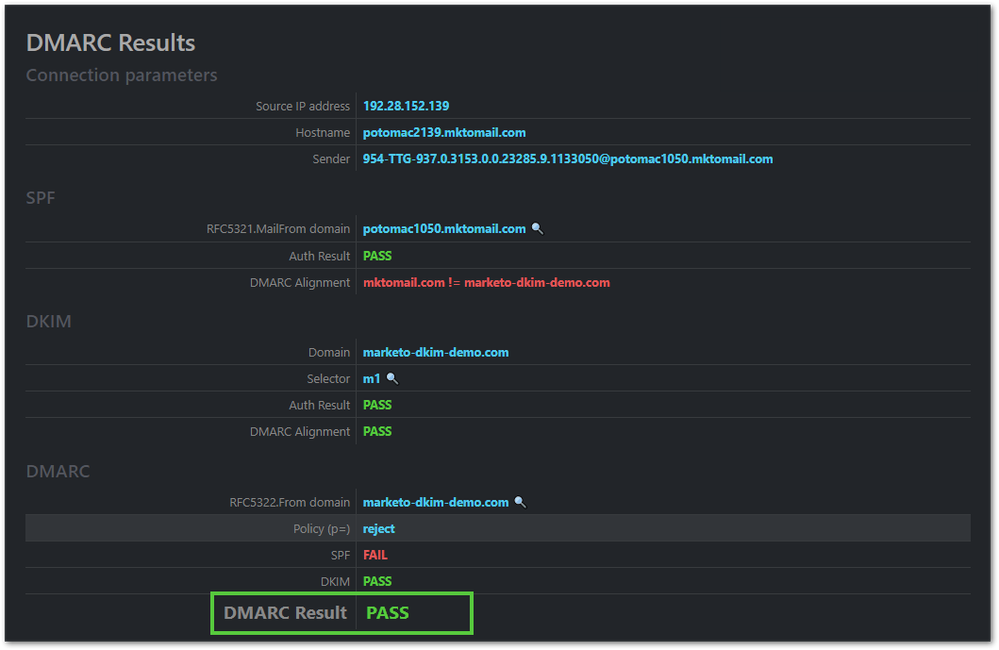
"v=DMARC1; p=reject;"When you send an email with the headers above, Marketo signs the email using the DKIM key for marketo-dkim-demo.com (since it’s marked Verified).[2]
The recipient’s anti-spam layer validates the DKIM signature. It also fetches your DMARC record, which says “Every email using From: user@marketo-dkim-demo.com must be DKIM-signed by marketo-dkim-demo.com, or else it isn’t legit and should be rejected.”[3]
No problem! Both DKIM and DMARC pass.[4] To the degree DKIM and DMARC affect deliverability, you’re in good shape:
To shakier ground
Now say you switch to using marketing.marketo-dkim-demo.com, without changing any other part of your config:[5]
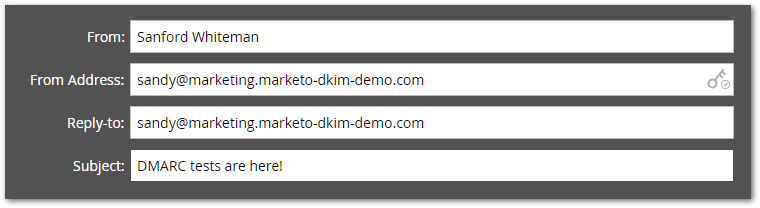
Marketo won’t stop you from using the subdomain, but now DMARC will fail, brutally dinging your deliverability:
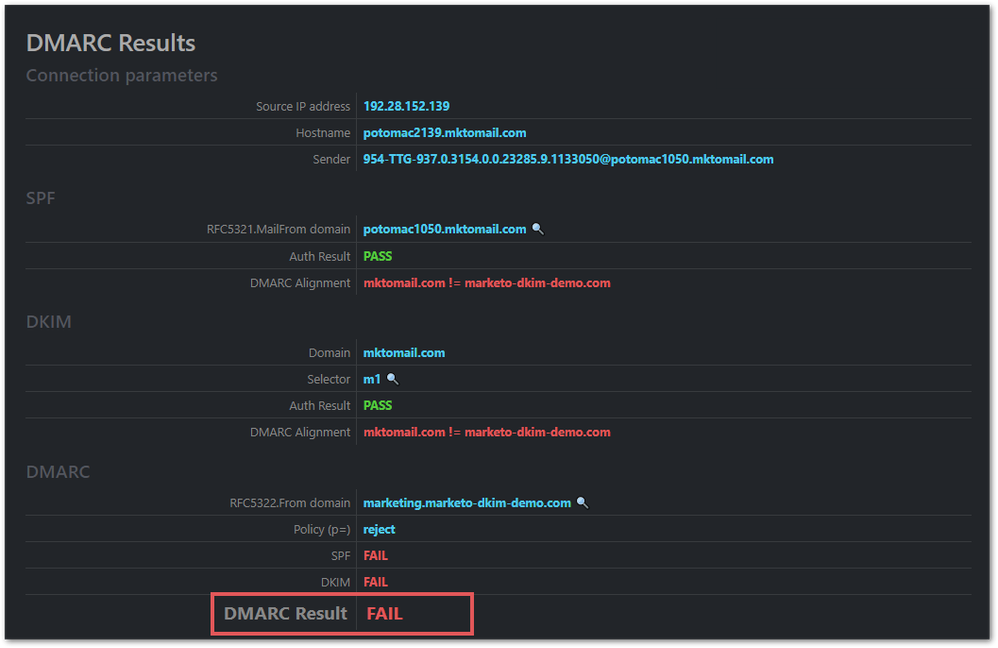
Why does this happen even though you don’t have a DMARC record at _dmarc.marketing.marketo-dkim-demo.com?
Because the subdomain has an implicit DMARC policy. Remember that you have a DMARC record at the parent:
"v=DMARC1; p=reject;"
This record doesn’t literally include the sp directive. But the DMARC spec says to use the p policy as the sp policy if it’s missing. So your record is processed as if it’s:
"v=DMARC1; p=reject; sp=reject"
sp=reject means any subdomain of marketo-dkim-demo.com comes down as hard as the parent. Therefore an unsigned email is a DMARC fail, just as it would be at the parent.
Proper fix vs. quick fix
The right thing to do: add the DKIM TXT record m1._domainkey.marketing.marketo-dkim-demo.com using the public key provided in Admin » Email.
If for some reason you can’t create that DKIM record immediately, but you can change the existing DMARC record for _dmarc.marketo-dkim-demo.com, add a temporary, explicit sp=none for now:
"v=DMARC1; p=reject; sp=none"
Alternately, create a DMARC record for the subdomain at _dmarc.marketing.marketo-dkim-demo.com (though it’s hard to imagine why you could create one TXT record subtype but not another):
"v=DMARC1; p=none"Credits
Screenshots are from the interactive tester at Learn DMARC, which is accurate and pretty to look at — though it does leave stuff out, like [2] below.
NOTES
[1] The DMARC record is even in relaxed mode — meaning SPF or DKIM alignment is theoretically easier to accomplish — yet that doesn’t help.
[2] Yes, it also signs with the builtin key for mktomail.com. That second signature isn’t relevant today, but if I left it out someone might call me on it!
[3] The assumption I make is you have a standard shared Marketo instance, without the custom branded envelope sender add-on. In this case, you can’t possibly pass SPF for marketo-dkim-demo.com. So by extension, you must pass DKIM or DMARC will fail.
[4] Again, the SPF check will pass in general. But it won’t pass for marketo-dkim-demo.com, it’ll pass for Marketo’s internal something.mktomail.com domain. Which is fine and good, but won’t help you pass DMARC.
[5] That is, you don’t add the new domain in Admin » Email. Though if you add it but don’t verify DKIM, the outcome is the same.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Copyright © 2025 Adobe. All rights reserved.
- Privacy
- Community Guidelines
- Terms of use
- Do not sell my personal information
Adchoices