Re: Marketo emails showing up as BULK - with no ability to show images
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
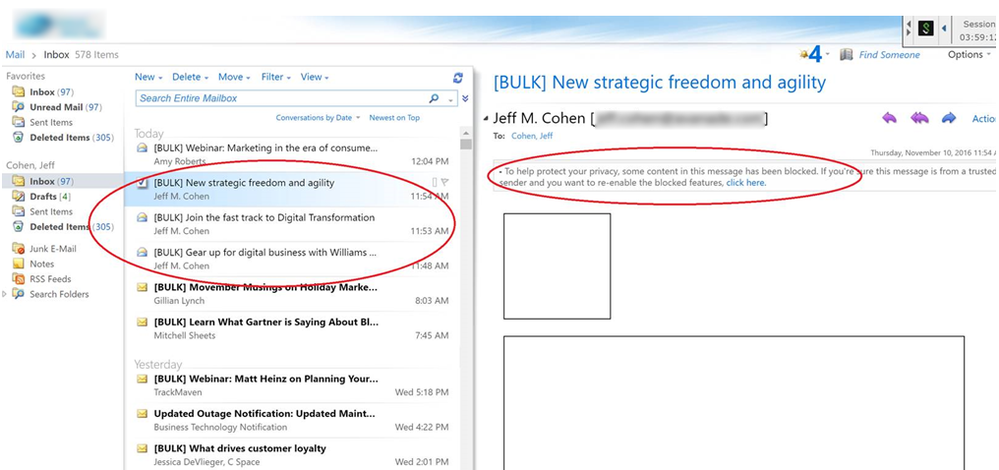
We've identified yet another client of ours who filter all Marketo emails as follows:
- When the email is sent, the words [BULK] are appended to the subject line
- Images are blocked
- When the user clicks the "click here" link to unblock all features (like images), the images remain broken/non-viewable.
Other than asking the client to whitelist our IP range (which hasn't worked with prior clients who have done this for us), is there anything we can do? We already have our SPF/DKIM setup properly, use branded tracking links, and send from our company's domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
From the screenshot, it looks like an intermediate server/service is changing the image src. I say this because OWA does not appear to be aware that clicking to enable images will have no effect. If you could get on a machine where this is happening it would be easy to see where those URLs are being rewritten to, and presumably figure out which software is making the change.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
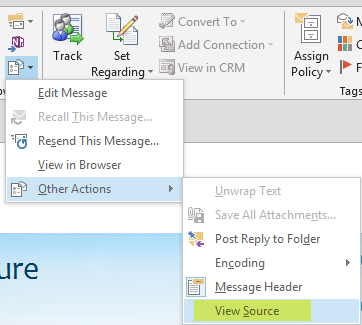
How do you view the source code of an email in OWA? When I click "view message details", it just provides the email header details and a bunch of encrypted code. In the Outlook desktop client, it's viewed here:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I think in OWA without extensions the best you have is view-source (that is, browser view-source).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
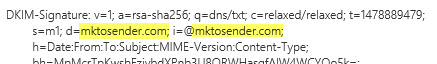
I started to look at the source and noticed in the email header that DKIM is signed by mktosender.com. Shouldn't this be our domain?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I started to look at the source and noticed in the email header that DKIM is signed by mktosender.com. Shouldn't this be our domain?
Certainly if you are publishing the DKIM pubkey on your domain then it should be using your domain. I think they've been mixing things up lately, but luckily it hasn't affected my "legacy" instances.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should I raise this issue with Marketo or our own IT team?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
You may see two DKIM signatures. One is your domain and the other is a Marketo domain.
If you don't see your domain also in a DKIM signature it may not be set up in the Marketo Admin console.
That particular signature indicates that you are sending from a subset of Marketo's IPs reserved for low volume, highly-vetted customers. I would definitely want to dig into these issues more keeping from a deliverability perspective.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
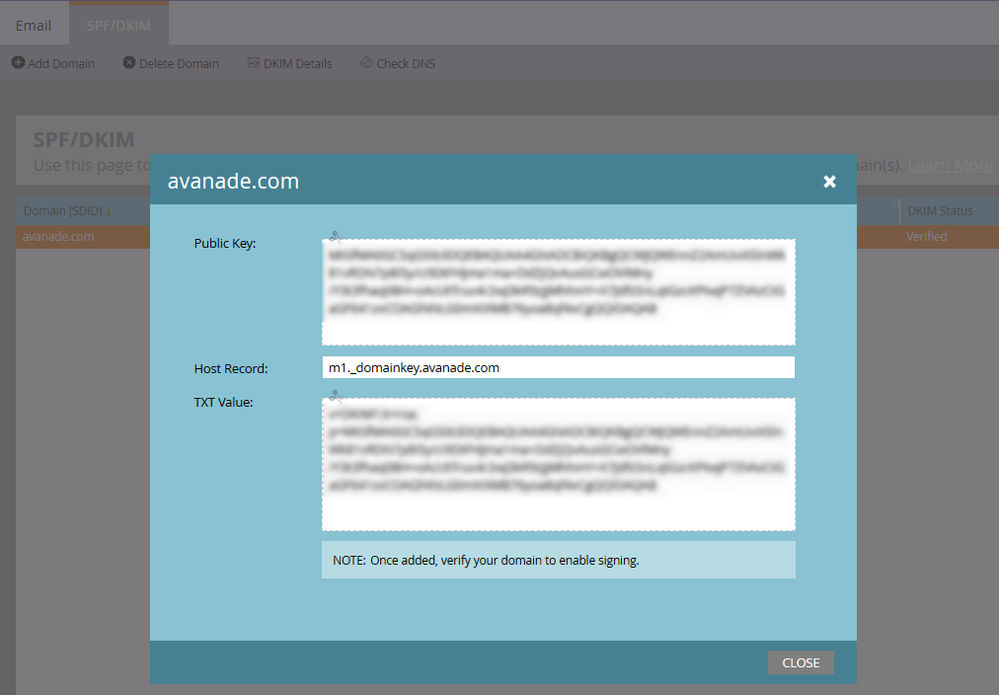
Kiersti, see the screenshot above - those are the only DKIM signatures found in our header. And yes, we have this configured in the Admin console:
I just submitted a ticket with Support and asked them to have the Deliverability team take a look at this.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I received the following response from Support:
What the Deliverability team told me is that we are dual-signing DKIM now. Meaning that in the chance that the customer has not set up DKIM, we're signing for them anyway. Dual-signing is fine and it doesn't affect deliverability at all.
What I don't get is that we have indeed setup our DKIM - and even if this is dual-signed (and we have setup DKIM properly) - why is our domain not listed in the DKIM signature within the header?
Sanford Whiteman, does this sound right?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Your domain must appear in the header if it's signed by your domain. Otherwise it's being single-signed only.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I just sent myself another test email and now notice dual DKIM signatures - it appears it was just enabled a litte while ago:
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/relaxed; t=1479161974;
s=m1; d=avanade.com; i=@avanade.com;
h=Date:From:To:Subject:MIME-Version:Content-Type;
DKIM-Signature: v=1; a=rsa-sha256; q=dns/txt; c=relaxed/relaxed; t=1479161974;
s=m1; d=mktosender.com; i=@mktosender.com;
h=Date:From:To:Subject:MIME-Version:Content-Type;
Is there any risk in having this signed by both our domain and Marketo's - especially if recipient email servers block all Marketo emails?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd add, too, that Marketo co-signing mail from trusted IPs (and not from untrusted IPs) is a good way to denote that those instances are at least somewhat policed/proper.
Whether "greater than zero trust" is enough to whitelist on in the real world is anothe matter.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
If you had a dedicated IP, which serves the purpose (to a degree) of obscuring the Marketo origins of your emails, then it could be questionable to opt back in to being Marketo-connected.
Otherwise, you'd be getting blocked by IP and/or envelope sender anyway, not by a 3rd-party DKIM signature.
Signing an email shows the recipient that there's someone taking end-to-end responsibility for the email content (as opposed to merely permitting the email server to use a sender domain, which is the best SPF can do). If the signer is the same as the From: address domain, that's considered a first-party or "author" signature -- the person who authored the content also signed it. That's the best use of DKIM.
If Marketo is throwing in a 3rd-party signature, that's not going to hurt anything unless the recipient blacklists or negatively weights by DKIM domain. That's pretty rare, but it can happen. DKIM is more often used for positive weighting. It's also a great tool for selective whitelisting because a recipient can say they allow emails that are *signed* and thus attributable to a given domain as opposed to emails that *claim* (via the forgeable From: or MAIL FROM:) to be from that domain.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Can anyone from Marketo's email deliverability team weigh in on this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dan,
Please reach out through Support on this issue to have this looked at by the Deliverability Team. There are a lot of reasons for bulk folder delivery that we would need to look into.
Delivery to the bulk folder is often driven by the reputation of the individual sender. Our team would start with high level questions about how the sender is acquiring their leads and how are they maintaining their database.
- Do they purchase email addresses? (Best Practices for Purchased Data)
- Do they remove inactive email addresses? (How to Manage Your Marketo Database for Deliverability)
- Have they recently triggered any blacklistings through Marketo? (Blacklist Remediation)
- We may also look into the content and see if there are any issue with the content that could be causing an issue.
-Kiersti
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI Dan,
Is this a large or small company?
In other terms, is this a feature of their in-house emailing servers or something provided by a ISP of any kind?
-Greg
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Greg - It's a very large, global company.
- Copyright © 2025 Adobe. All rights reserved.
- Privacy
- Community Guidelines
- Terms of use
- Do not sell my personal information
Adchoices