- Marketing Nation
- :
- Products
- :
- Product Discussions
- :
- Re: Does this look like a SQL/PHP injection to you...
Your Achievements
Next /
Sign inSign in to Community to gain points, level up, and earn exciting badges like the new Applaud 5 BadgeLearn more!
View All BadgesSign in to view all badges
Re: Does this look like a SQL/PHP injection to you?
Topic Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2014
01:32 PM
01-08-2014
01:32 PM
Does this look like a SQL/PHP injection to you?
While sending myself a sample email, I noticed the “Lead” drop-down completely filled with the following:
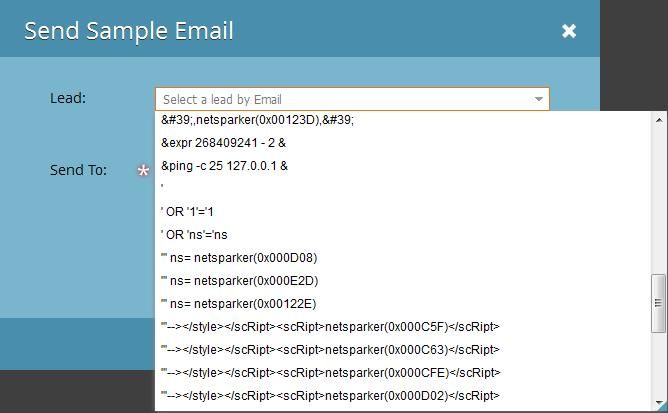
These appear to be SQL/PHP injections or DoS attacks. Does Marketo not have any preventative measures for these entering the system as leads?

These appear to be SQL/PHP injections or DoS attacks. Does Marketo not have any preventative measures for these entering the system as leads?
Labels:
3 REPLIES 3
Anonymous
Not applicable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2014
02:01 PM
01-08-2014
02:01 PM
Re: Does this look like a SQL/PHP injection to you?
Fascinating!
Marketo does have SQL injection protection, obviously, but apparently not something built-in to keep your database clean from these junk values.
The interesting part to me is that these wouldn't be valid email addresses with their pattern. There is client-side form validation eliminating people manually trying to get past keyboard-slamming in the email field, but apparently not server-side validation of these fields. Someone trying to get past that protection can easily turn off JS and submit whatever they want in the form.
You could easily set up some smart lists/smart campaigns watching for irregular email values if this continues to be a problem, and delete those leads. Any email address containing "<, ', /, &, #, -" etc. I'm sure you could find other patterns within the leads themselves, the other fields that are available, and cast your own comprehensive net to catch/delete these false leads.
You also could set up an alert for "new lead created with weird symbol value" that goes to an admin, if you think there's someone manually trying to hack into your system. That will be an overwhelming amount of emails if it's a bot doing it, though.
Best,
Edward Unthank
Marketing Operations Specialist
Yesler
Marketo does have SQL injection protection, obviously, but apparently not something built-in to keep your database clean from these junk values.
The interesting part to me is that these wouldn't be valid email addresses with their pattern. There is client-side form validation eliminating people manually trying to get past keyboard-slamming in the email field, but apparently not server-side validation of these fields. Someone trying to get past that protection can easily turn off JS and submit whatever they want in the form.
You could easily set up some smart lists/smart campaigns watching for irregular email values if this continues to be a problem, and delete those leads. Any email address containing "<, ', /, &, #, -" etc. I'm sure you could find other patterns within the leads themselves, the other fields that are available, and cast your own comprehensive net to catch/delete these false leads.
You also could set up an alert for "new lead created with weird symbol value" that goes to an admin, if you think there's someone manually trying to hack into your system. That will be an overwhelming amount of emails if it's a bot doing it, though.
Best,
Edward Unthank
Marketing Operations Specialist
Yesler
Anonymous
Not applicable
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2014
02:10 PM
01-08-2014
02:10 PM
Re: Does this look like a SQL/PHP injection to you?
Among other, we have nightly smart campaigns to mark any such kind of email address records as invalid.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
01-08-2014
02:18 PM
01-08-2014
02:18 PM
Re: Does this look like a SQL/PHP injection to you?
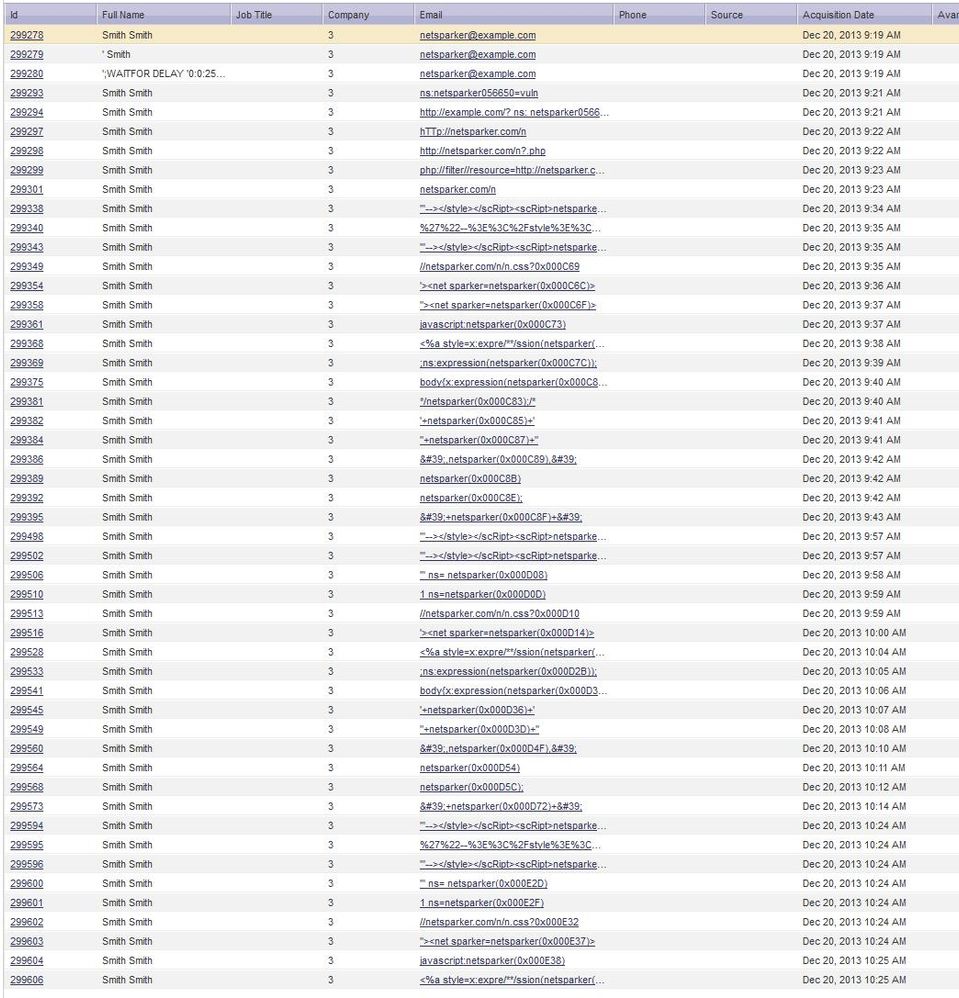
After further investigating, there were about 200 of these records that entered our system on Dec. 20th (from a form on our Swedish site).

- Copyright © 2025 Adobe. All rights reserved.
- Privacy
- Terms of use
- Do not sell my personal information
Adchoices

.png)